Internet connectivity is of paramount importance for both corporate and educational institutions. It serves as the backbone for communication, collaboration, research, and overall operations.
Broadband Internet Access
Broadband Internet access is a high-speed, always-on internet connection that allows for faster data transmission compared to traditional dial-up connections. It provides users with reliable and continuous access to the internet, enabling various online activities, including web browsing, streaming media, online gaming, video conferencing, and more. Here are key aspects of broadband Internet access:
Speed and Capacity: Broadband connections offer significantly higher speeds than dial-up connections, typically measured in megabits per second (Mbps) or gigabits per second (Gbps). These faster speeds enable quick downloads, smooth streaming, and efficient data transmission.
Types of Broadband Connections:
- DSL (Digital Subscriber Line): DSL uses existing telephone lines to provide broadband internet access. It offers different variations, such as ADSL (Asymmetric DSL) and VDSL (Very-high-bit-rate DSL).
- Cable Internet: Cable broadband utilizes the same coaxial cables that deliver cable television services. It’s known for its fast download speeds.
- Fiber-Optic Internet: Fiber-optic broadband uses optical fibers to transmit data as pulses of light. It’s known for its extremely high-speed capabilities and low latency.
- Wireless Broadband: Wireless broadband includes technologies like Wi-Fi, 4G LTE, and 5G. It enables internet access without physical cables and is widely used for mobile devices and home networks.
- Satellite Internet: Satellite broadband connects users to the internet via satellite signals. It’s often used in rural or remote areas where other broadband options are limited.
Always-On Connection: Broadband connections are “always on,” meaning users do not need to establish a connection each time they want to access the internet. This contrasts with dial-up connections, which require users to connect and disconnect for each session.
Simultaneous Use: Broadband connections support multiple devices simultaneously, making it suitable for households with multiple users and various internet-connected devices.
Applications and Services: Broadband access enables users to engage in bandwidth-intensive activities, such as streaming high-definition videos, participating in online gaming, video conferencing, and cloud computing.
High-Quality Media Streaming: With broadband, users can stream high-quality video and audio content from services like Netflix, YouTube, Spotify, and more, without buffering or interruptions.
Business and Education: Broadband is essential for businesses, educational institutions, and government organizations, supporting various online operations, virtual meetings, e-learning, and remote work.
Economic and Social Impact: Access to reliable broadband is seen as a driver of economic growth and social inclusion. It facilitates online entrepreneurship, e-commerce, telemedicine, and access to information and services.
Infrastructure Investment: Expanding and improving broadband infrastructure, particularly in underserved or rural areas, is a priority for many governments and telecommunications companies to bridge the digital divide.
Speed Tiers: Broadband plans often come in different speed tiers, allowing users to choose the level of bandwidth that suits their needs and budget.
Quality of Service (QoS): Broadband providers may implement Quality of Service policies to prioritize certain types of traffic, ensuring a consistent and reliable experience for critical applications.
Broadband Internet access has become a fundamental part of modern life, enabling a wide range of online activities and contributing to economic development and connectivity in both urban and rural areas. The availability and quality of broadband services can vary by region and provider, but efforts continue to expand access and improve internet connectivity worldwide.
Best Practices
Redundancy and Failover
Internet connectivity redundancy and failover are critical strategies to ensure uninterrupted access to the internet and maintain business continuity in the event of a network outage or disruption. Here’s an overview of redundancy and failover in internet connectivity:
Redundancy:
- Redundancy involves having duplicate or backup systems, connections, or resources in place to provide continuous operation in case of failure. In terms of internet connectivity, redundancy typically refers to having multiple internet service providers (ISPs) or connections.
Failover:
- Failover is the automatic or manual process of switching from a primary connection or system to a backup (secondary) connection or system when the primary experiences a failure. In the context of internet connectivity, failover ensures seamless access to the internet when the primary connection goes down.
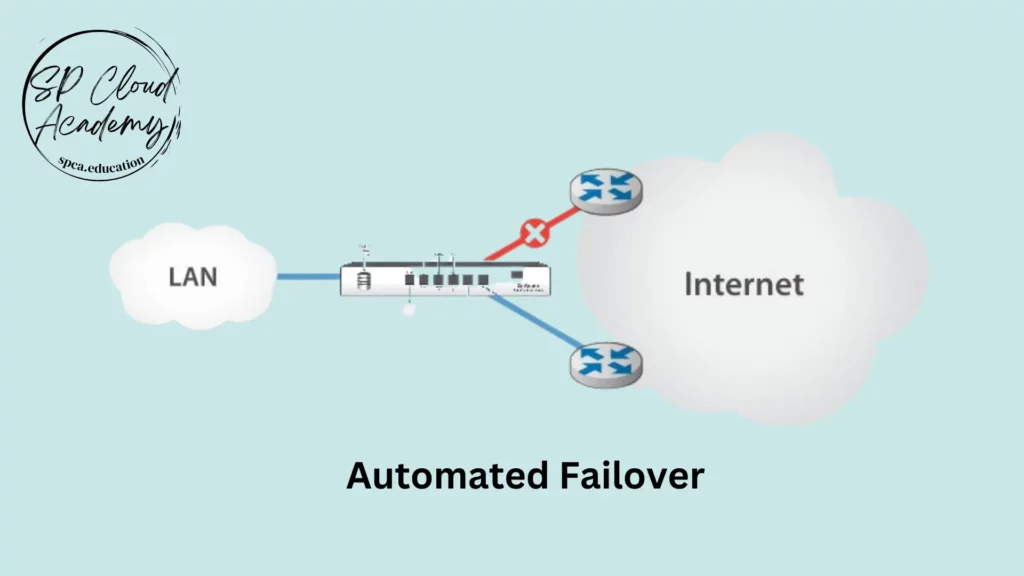
Key Components of Redundancy and Failover:
Primary and Secondary Connections:
- The primary internet connection is the main connection that the organization uses for daily operations. The secondary connection serves as a backup.
Load Balancing:
- Load balancing distributes network traffic across multiple connections to optimize performance and minimize the risk of overloading a single connection. It can be used alongside redundancy for added efficiency.
Automatic Failover:
- Automatic failover systems detect when the primary connection experiences a failure and automatically switch to the secondary connection without manual intervention. This minimizes downtime.
Manual Failover:
- In some cases, organizations may choose to manually initiate failover to the secondary connection based on specific criteria or preferences.
Monitoring and Alerts:
- Network monitoring tools continuously assess the status of primary and secondary connections. If an issue is detected, administrators are alerted, allowing them to take action promptly.
Testing and Simulation:
- Regularly test failover procedures to ensure they work as expected. Simulate scenarios to evaluate the response of failover systems and identify any potential issues.
Benefits of Internet Connectivity Redundancy and Failover:
- Business Continuity: Redundancy and failover ensure that the organization’s critical internet-dependent operations can continue even in the face of ISP outages or other connectivity issues.
- Minimal Downtime: Automatic failover minimizes downtime, ensuring that employees can continue working and customers can access online services without interruption.
- Load Distribution: Load balancing and redundancy can optimize network performance by distributing traffic across multiple connections, preventing congestion on a single link.
- Enhanced Reliability: Organizations can rely on multiple ISPs or connections, reducing the risk of a single point of failure affecting internet access.
- Disaster Recovery: In the event of a disaster or network disruption, redundancy and failover can help organizations maintain essential communication and data access.
Considerations for Implementing Redundancy and Failover:
- Cost: Redundancy and failover solutions may involve additional costs, including the expense of a backup connection and any hardware or software required for implementation.
- Configuration: Properly configure routers, firewalls, and network equipment to manage redundancy and failover effectively. Seek assistance from IT professionals if needed.
- Testing: Regularly test your failover setup to ensure it functions as expected. This includes simulating primary connection failures and observing the transition to the secondary connection.
- Provider Selection: When choosing ISPs for redundancy, consider providers with diverse infrastructure and routing to minimize the likelihood of both connections being affected by the same issue.
- Security: Ensure that security measures are consistently applied to both primary and secondary connections to protect against cyber threats.
Internet connectivity redundancy and failover are vital components of a robust network infrastructure, providing the assurance that an organization’s internet-dependent operations can continue running smoothly, even when faced with connectivity challenges.
Bandwidth Management
Bandwidth management is crucial for optimizing and prioritizing the use of corporate internet connectivity. Effectively managing bandwidth ensures that critical business applications and services have the necessary network resources while preventing non-essential activities from degrading network performance.
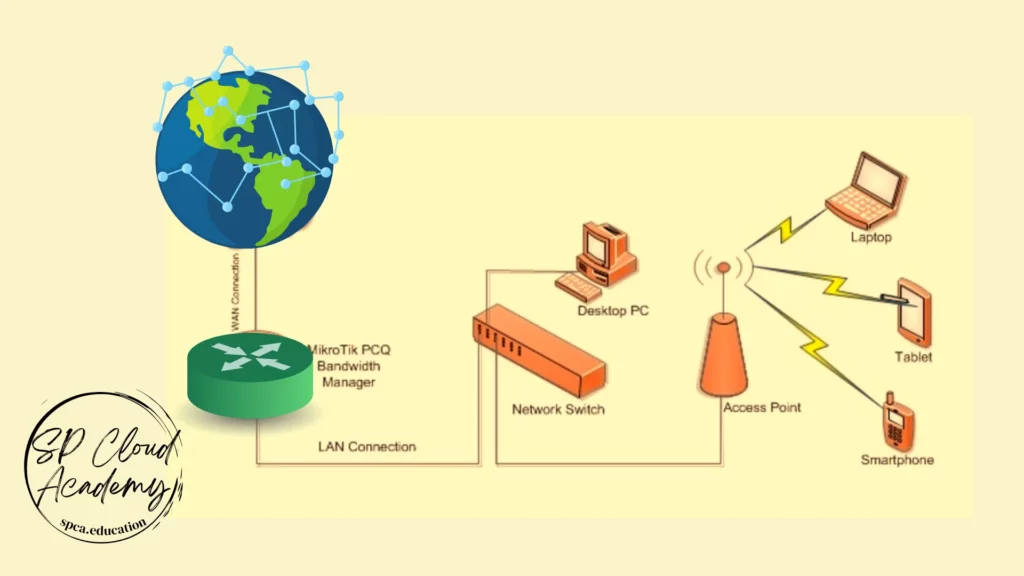
Here are best practices for bandwidth management:
1. Network Traffic Analysis:
- Start by analyzing your network traffic to understand which applications and services consume the most bandwidth. Use network monitoring tools to identify bandwidth-hungry applications.
2. Define Business Priorities:
- Identify critical business applications and services that require high-priority access to the internet. These may include VoIP, video conferencing, and cloud-based business tools.
3. Implement Quality of Service (QoS):
- QoS allows you to prioritize network traffic based on application or service type. You can assign higher priority to business-critical applications to ensure they have the necessary bandwidth.
4. Bandwidth Allocation:
- Allocate specific bandwidth quotas for different types of traffic. For instance, you can reserve a portion of your bandwidth for VoIP traffic to ensure call quality.
5. Rate Limiting:
- Implement rate limiting or bandwidth caps for non-essential applications and services to prevent them from consuming excessive bandwidth. Common examples include streaming media and non-work-related downloads.
6. Traffic Shaping:
- Use traffic shaping to control the flow of data and prevent network congestion. It helps ensure that bandwidth is evenly distributed among users and applications.
7. Prioritize Critical Users or Departments:
- Assign higher bandwidth allocations or priorities to users or departments that require it for their daily tasks. This ensures that key personnel have reliable access to critical resources.
8. Web Filtering and Content Control:
- Implement content filtering solutions to block access to non-work-related websites, streaming services, and other bandwidth-intensive platforms during business hours.
9. Application Optimization:
- Employ application optimization techniques, such as caching and compression, to reduce the amount of bandwidth required for certain applications and services.
10. Peak Usage Scheduling:
Schedule non-essential or bandwidth-intensive tasks during non-peak hours to minimize their impact on network performance during business hours.
11. Monitor and Adjust:
Continuously monitor network traffic and bandwidth usage to identify trends and make necessary adjustments to your bandwidth management policies.
12. Employee Education:
Educate employees about responsible internet usage and the impact of bandwidth-heavy activities on network performance. Encourage them to use bandwidth-intensive applications during non-peak hours.
13. Regular Updates:
Regularly review and update your bandwidth management policies to adapt to changing business needs and technology trends.
14. Bandwidth Expansion:
If your organization’s bandwidth requirements consistently exceed your capacity, consider upgrading your internet connection to meet growing demands.
15. Disaster Recovery Planning:
Develop a disaster recovery plan that includes bandwidth allocation priorities in case of network failures or emergencies.
Effective bandwidth management is essential to ensure that your organization’s critical operations run smoothly without disruptions caused by bandwidth congestion. By implementing these best practices, you can optimize your corporate internet connectivity and maintain high performance for essential business functions while controlling non-essential usage.
Prevent system losses
Optimizing end devices in organizational sectors can play a significant role in preventing system losses related to internet connectivity. Efficiently managing and configuring the devices that connect to your network can enhance performance, security, and overall reliability. Here are strategies to prevent system losses through end device optimization:
1. Device Management Policies:
- Develop and enforce device management policies that specify the types of devices allowed on the network, including laptops, desktops, mobile devices, and IoT devices. This helps maintain control over the network environment.
2. Endpoint Security:
- Install and regularly update antivirus software and anti-malware tools on all end devices. Implement endpoint security solutions to protect against threats such as ransomware and phishing attacks.
3. Patch Management:
- Establish a patch management system to ensure that all operating systems and software on end devices are up to date with the latest security patches and updates. Vulnerabilities in outdated software can be exploited by attackers.
4. Network Access Control (NAC):
- Implement NAC solutions to enforce security policies and ensure that only authorized and properly configured devices can access the network. NAC can quarantine non-compliant or suspicious devices.
5. Mobile Device Management (MDM):
- If your organization allows mobile devices, implement an MDM solution to manage and secure them. MDM enables remote configuration, monitoring, and security enforcement for smartphones and tablets.
6. User Education and Training:
- Educate employees about responsible device usage and cybersecurity best practices. Teach them how to recognize and report potential threats like suspicious emails or unusual device behavior.
7. Application Whitelisting:
- Consider whitelisting approved applications to prevent the installation and execution of unauthorized or potentially harmful software on end devices.
8. Password Policies:
- Enforce strong password policies for all devices and accounts. Encourage the use of password managers and two-factor authentication (2FA) to enhance security.
9. Remote Device Wiping:
- Implement the ability to remotely wipe data from lost or stolen devices to protect sensitive information.
10. VPN Usage:
– Require the use of Virtual Private Networks (VPNs) for remote access to the organization’s network. VPNs provide a secure and encrypted connection, especially when accessing the internet from public networks.
11. Device Monitoring and Reporting:
– Continuously monitor end devices for suspicious activities or security breaches. Implement reporting mechanisms to quickly identify and respond to anomalies.
12. Regular Audits and Assessments:
– Conduct periodic security audits and vulnerability assessments of end devices to identify and remediate security weaknesses.
13. Device Decommissioning:
– Develop a process for properly decommissioning and securely disposing of end-of-life devices to prevent data leakage.
14. Network Segmentation:
– Segment your network to separate devices based on their roles and security requirements. This limits the potential impact of security breaches or compromised devices.
15. Guest Network Isolation:
– Isolate guest networks from the primary network to prevent unauthorized access to sensitive information and internal resources.
16. User Accountability:
– Implement user accountability measures, such as logging and auditing, to trace actions taken on end devices and identify potential security incidents.
End device optimization is an integral part of maintaining a secure and reliable network. By implementing these strategies and fostering a culture of cybersecurity awareness within your organization, you can significantly reduce the risk of system losses related to internet connectivity issues and security threats originating from end devices.
Use Proxy and CDN
Using a combination of a proxy server and Content Delivery Network (CDN) can indeed help speed up internet connectivity and enhance web performance. These technologies work together to optimize content delivery and reduce latency. Here’s how they can be used effectively:
1. Proxy Servers:
- A proxy server acts as an intermediary between a user’s device and the internet. It can serve multiple purposes, including enhancing speed, security, and privacy. Here’s how a proxy server can improve internet connectivity: a. Caching:
- Proxy servers can cache frequently requested web content locally. When a user requests that content again, the proxy server can serve it directly from its cache, reducing the need to fetch it from the origin server. This can significantly speed up the loading of web pages and reduce bandwidth usage.
- Proxy servers can distribute incoming traffic across multiple servers or data centers. This load balancing ensures that requests are handled efficiently, reducing server load and improving response times.
- Proxies can compress data before sending it to the user’s device. This reduces the amount of data that needs to be transmitted over the internet, resulting in faster load times for web pages and resources.
- Proxies can also enhance security by acting as a barrier between users and potentially malicious content. They can filter out harmful web traffic and protect against certain types of cyber threats.
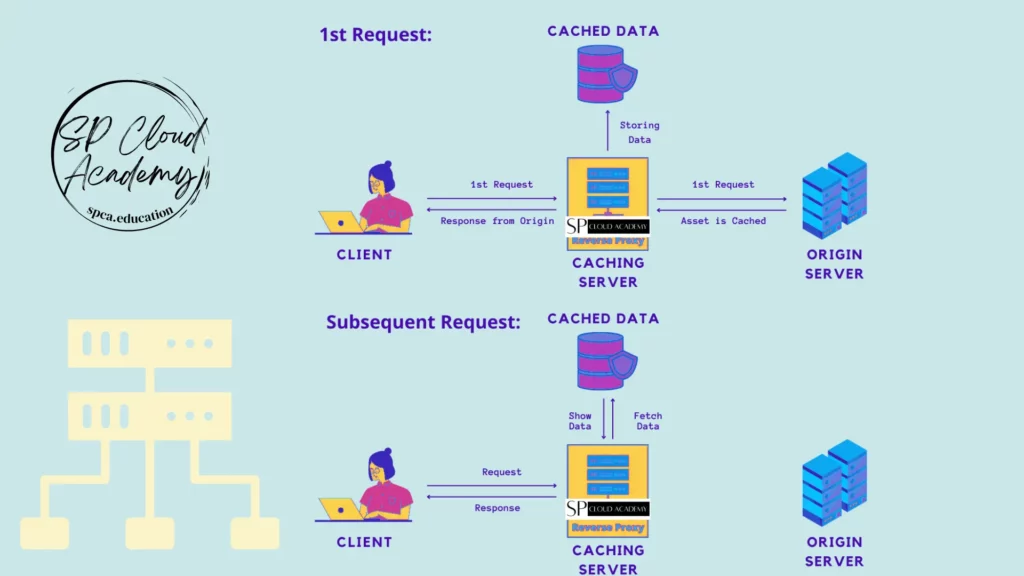
2. Content Delivery Networks (CDNs):
- CDNs are networks of geographically distributed servers that store and deliver web content, such as images, videos, stylesheets, and scripts, from locations closer to the end user. Here’s how CDNs can speed up internet connectivity: a. Reduced Latency:
- CDNs store copies of website content on servers located in multiple geographic regions. When a user requests a web page, the CDN delivers content from the server nearest to the user. This reduces the physical distance data must travel, resulting in lower latency and faster load times.
- CDNs are designed to handle high volumes of traffic efficiently. They can automatically scale to accommodate spikes in web traffic, ensuring that websites remain responsive even during traffic surges.
- CDNs often include distributed denial-of-service (DDoS) protection mechanisms to defend against malicious traffic and keep websites accessible during DDoS attacks.
Using Proxy Servers and CDNs Together:
- To maximize the benefits of both technologies, organizations often use proxy servers in conjunction with CDNs. Here’s how they work together: a. CDN Integration:
- Organizations configure their proxy servers to work seamlessly with their chosen CDN. When a user requests a web page, the proxy server can direct requests to the CDN’s servers, which then deliver cached content to the user.
- Proxy servers can cache content from the CDN as well. This dual caching strategy ensures that frequently requested content is stored locally on both the proxy server and the CDN’s servers, further reducing load times.
- Proxy servers can intelligently route requests to the appropriate CDN server, taking into account factors like server load and proximity to the user.
Using a proxy server and CDN in tandem can provide a powerful solution for speeding up internet connectivity, reducing latency, and improving overall web performance for both end users and organizations hosting web content.
Implement Firewall
Firewalls are an essential tool for securing and controlling access to specific content on the internet. They act as a barrier between your network and the external internet, allowing you to define and enforce rules and policies for content access.
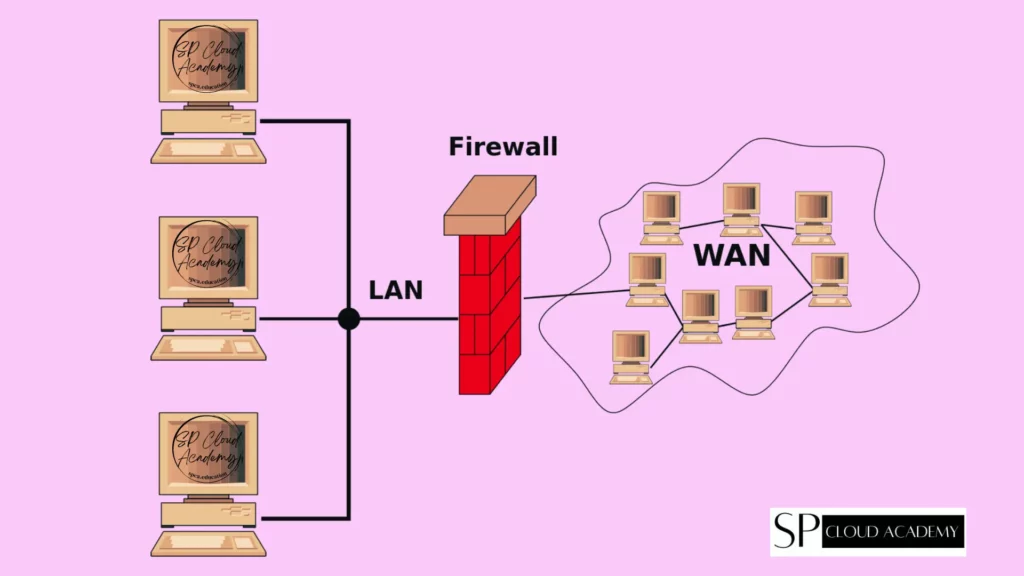
Here’s how you can use firewalls to secure and control internet content access:
1. Stateful Packet Inspection:
- Firewalls can perform stateful packet inspection, which examines network traffic and makes decisions based on the state of active connections. This helps prevent unauthorized access and can be used to block specific content or websites.
2. Application Layer Filtering:
- Next-generation firewalls (NGFWs) offer application layer filtering capabilities. They can identify and control traffic at the application layer, allowing you to block or allow specific applications and services, such as social media, file sharing, or streaming services.
3. Content Filtering:
- Use content filtering features in firewalls to restrict access to specific websites or types of content based on categories, keywords, or URLs. This is often used in educational institutions and workplaces to enforce internet usage policies.
4. URL Filtering:
- Configure URL filtering rules to block or allow access to specific websites or web categories. You can create white-lists (allow only specific sites) or blacklists (block specific sites) to control access.
5. Intrusion Detection and Prevention:
- Many firewalls have intrusion detection and prevention systems (IDPS) that can identify and block malicious content or activities, including malware downloads and phishing attempts.
6. Geolocation Filtering:
- Implement geolocation-based filtering to restrict access from certain geographic regions. This can enhance security by blocking access from known high-risk areas.
7. Time-Based Rules:
- Create time-based rules to allow or restrict access to specific content during certain hours or days. For example, you can block access to social media sites during working hours.
8. User Authentication:
- Implement user authentication through technologies like LDAP or Active Directory. This allows you to apply content filtering rules based on individual user accounts, ensuring that specific users have the appropriate access.
9. VPN Filtering:
- If your organization uses VPNs (Virtual Private Networks), configure your firewall to inspect VPN traffic. This helps ensure that content filtering policies apply even when users are connected via VPN.
10. Logging and Reporting:
– Enable firewall logging to track and monitor internet traffic. Regularly review logs and generate reports to identify trends, security threats, and policy violations.
11. Regular Updates:
– Keep your firewall’s firmware and signature databases up to date to ensure it can effectively identify and block new threats and content.
12. Compliance and Privacy:
– Ensure that your content filtering practices comply with relevant regulations and respect user privacy. Transparent communication about content filtering policies is essential.
Effective firewall configuration and management are critical for maintaining a secure and productive network environment. By using firewalls to control and secure internet content access, organizations can mitigate security risks, enforce internet usage policies, and ensure that users have safe and appropriate access to online resources.
Deploy Powerfull and Reliable Hardware
Deploying powerful and reliable hardware is a fundamental step in ensuring strong internet connectivity for your organization. High-quality hardware can provide the necessary performance, stability, and scalability to meet your connectivity needs. Here are key components and considerations for deploying powerful and reliable hardware for internet connectivity:
1. Network Routers:
- Invest in enterprise-grade routers that can handle high volumes of network traffic. Choose routers that support advanced features like Quality of Service (QoS), load balancing, and failover for enhanced performance and reliability.
2. Switches:
- Use managed switches to create a robust and scalable network infrastructure. Managed switches offer features such as VLAN support, port mirroring, and Quality of Service (QoS) for efficient traffic management.
3. Firewalls and Security Appliances:
- Deploy robust firewall appliances and security devices to protect your network from cyber threats. Consider next-generation firewalls (NGFWs) with advanced threat detection and prevention capabilities.
4. Load Balancers:
- Implement load balancers to distribute network traffic evenly across multiple servers or internet connections. This enhances network performance and ensures high availability.
5. Access Points (APs):
- Deploy high-quality wireless access points for Wi-Fi connectivity. Ensure they support the latest Wi-Fi standards and provide sufficient coverage for your premises.
6. Modems and Gateways:
- Choose reliable modems or gateways for your internet connections. Consider redundancy with multiple ISPs for failover capabilities.
7. Network Attached Storage (NAS):
- Use NAS devices for efficient storage and data management. This can enhance file sharing and backup capabilities.
8. Uninterruptible Power Supplies (UPS):
- Install UPS units to provide backup power during electrical outages. This ensures that critical network equipment remains operational.
9. Redundancy and Failover:
- Implement redundancy for critical network components, including internet connections, routers, and switches. This minimizes downtime and ensures continuity in case of hardware failures.
10. Scalability:
– Plan for future growth by choosing hardware that can scale to accommodate increased network traffic and additional devices. This prevents bottlenecks as your organization expands.
11. Remote Management:
– Invest in hardware with remote management capabilities, allowing IT administrators to monitor and configure devices remotely. This is especially important for troubleshooting and maintenance.
12. Regular Maintenance:
– Schedule regular maintenance and firmware updates for your hardware. Keeping equipment up to date helps ensure optimal performance and security.
13. Redundant Power Supplies:
– For critical hardware components, consider devices with redundant power supplies to minimize the risk of power-related failures.
14. Quality Brands and Support:
Choose hardware from reputable brands known for reliability and performance. Ensure that there is readily available technical support in case of issues.
15. Documentation and Inventory:
Maintain detailed documentation of your network hardware, including configurations and inventory. This facilitates troubleshooting and planning for upgrades.
16. Budget for Future Upgrades:
Allocate budget for future hardware upgrades and replacements. Hardware has a finite lifespan, and planning for its eventual replacement is essential for long-term reliability.
By investing in powerful and reliable hardware and maintaining it effectively, you can establish a strong foundation for internet connectivity that meets your organization’s performance, security, and scalability requirements.
Regular Updates and Patch Management
Regular updates and patch management are critical aspects of maintaining a secure and efficient corporate internet connectivity infrastructure. Keeping your network devices, software, and security measures up to date helps protect against vulnerabilities, enhances performance, and ensures a reliable internet connection. Here’s a guide to regular updates and patch management for corporate internet connectivity:
1. Network Equipment:
- Routers, Switches, and Firewalls: Keep the firmware of your network equipment up to date. Manufacturers release updates to address security vulnerabilities, improve performance, and add new features. Regularly check for firmware updates and apply them according to a schedule.
- Load Balancers and Proxy Servers: Apply updates and patches to load balancers and proxy servers to maintain their functionality and security. Ensure that these devices are included in your patch management plan.
- Wireless Access Points (APs): Update the firmware of wireless APs to enhance security and support for new Wi-Fi standards. Consider a centralized management system for easier AP firmware management.
2. Operating Systems:
- Regularly update the operating systems (OS) of servers, workstations, and network devices. Enable automatic updates where possible to ensure that security patches are applied promptly.
3. Security Software:
- Firewalls and Intrusion Detection/Prevention Systems (IDPS): Keep security software, including firewalls and IDPS, up to date with the latest threat definitions and patches. This ensures that your network remains protected against evolving threats.
- Antivirus and Antimalware: Maintain up-to-date antivirus and antimalware software on all devices. Schedule regular scans and updates to protect against malware.
4. Web Browsers:
- Ensure that web browsers on all devices are updated to the latest versions. Modern browsers often include security enhancements and performance improvements.
5. VPN Clients:
- If your organization uses VPNs, regularly update VPN client software to ensure secure and reliable remote access.
6. Content Filtering and Security Solutions:
- Keep content filtering and other security solutions, such as web application firewalls (WAFs), updated with the latest threat intelligence and security patches.
7. Third-Party Applications:
- Regularly update third-party applications and software used by your organization. Vulnerabilities in these applications can be exploited by attackers.
8. Vulnerability Scanning:
- Conduct regular vulnerability assessments and scanning of your network infrastructure to identify weaknesses. Address identified vulnerabilities promptly through patching and remediation.
9. Patch Management Process:
- Establish a formal patch management process that includes the following steps:
- Identify and prioritize critical patches based on severity and potential impact.
- Test patches in a controlled environment before applying them to production systems.
- Develop a deployment schedule that minimizes disruption to business operations.
- Maintain a rollback plan in case issues arise after patch deployment.
10. Change Management:
- Integrate patch management into your organization’s change management process to ensure that updates are systematically tracked, tested, and deployed.
11. Monitoring and Alerts:
- Implement network monitoring tools that provide alerts for critical events, including missing patches or security vulnerabilities. Proactive monitoring allows for quick response to issues.
12. Employee Training:
- Educate employees about the importance of software updates and patches. Encourage them to promptly install updates on their devices.
13. Documentation:
- Maintain detailed documentation of your patch management activities, including patch schedules, deployment records, and testing results.
Effective patch management is an essential component of cybersecurity and network reliability. By staying proactive and systematic in your approach to updates and patches, you can significantly reduce the risk of security breaches and network disruptions related to corporate internet connectivity.
Deploy local update facilities
Deploying local update facilities, such as a local content delivery network (CDN) or a software update server, is an effective strategy to save valuable organizational internet bandwidth. This approach allows you to distribute updates, patches, and software packages internally, reducing the need to download these files repeatedly from the internet. Here’s how you can set up local update facilities to achieve bandwidth savings:
1. Local Content Delivery Network (CDN):
- A local CDN stores copies of frequently accessed content, including software updates and patches, on servers within your organization’s network. This minimizes the need to fetch these files from external sources, conserving internet bandwidth.
- Choose a CDN solution that supports the caching and distribution of updates for the operating systems and software used in your organization.
- Configure the CDN to automatically update its content repository with the latest patches and updates from trusted sources.
- Implement geographically distributed CDN servers to reduce latency and ensure fast access to updates for all network locations.
2. Software Update Server:
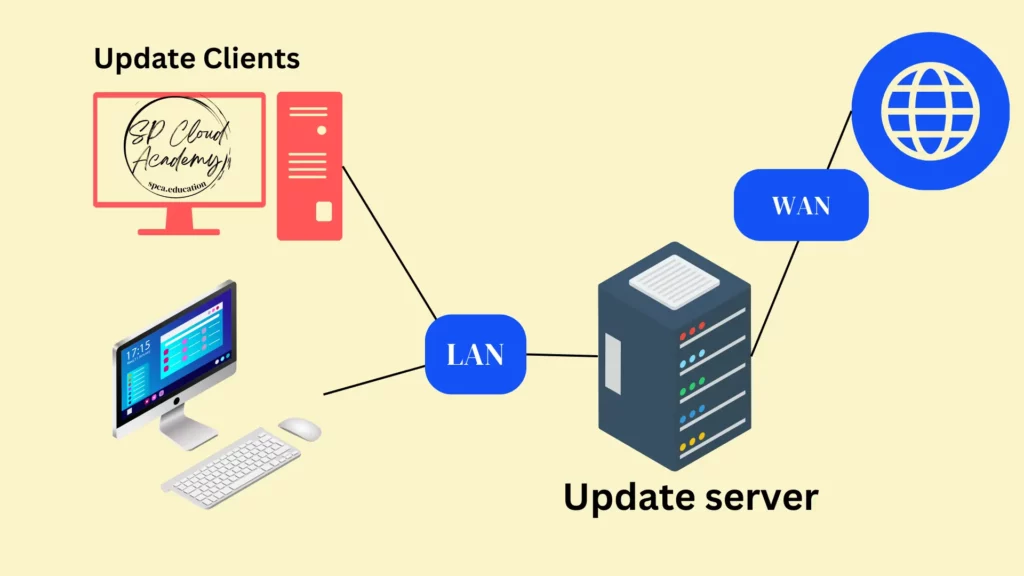
- Set up a dedicated software update server within your organization’s network. This server will host and distribute updates for the operating systems and applications used by your employees.
- For Microsoft Windows environments, consider using Windows Server Update Services (WSUS) to manage and distribute Windows updates internally.
- For Linux distributions, create a local mirror repository that hosts updates for your chosen distributions. Tools like apt-mirror and rsync can help maintain these repositories.
- Ensure that the update server is regularly synchronized with official software repositories to provide the latest updates to your users.
3. Package Caching:
- Implement package caching solutions that store downloaded updates and software packages on a local server. Tools like Squid for HTTP/HTTPS traffic and apt-cacher-ng for Debian-based systems can be used for caching.
- Devices on your network will fetch updates and packages from the local cache instead of downloading them from the internet, saving bandwidth.
4. Group Policy and Configuration Management:
- Use group policy settings (for Windows environments) or configuration management tools (such as Puppet or Ansible) to configure devices to retrieve updates and patches from the local update facilities.
5. Monitoring and Reporting:
- Implement monitoring and reporting mechanisms to track bandwidth savings, update server status, and ensure that updates are being distributed effectively.
6. Testing and Quality Assurance:
- Before deploying updates from your local facilities, ensure that they are tested in a controlled environment to verify compatibility and stability.
7. User Education:
- Educate employees about the benefits of using local update facilities, such as faster update downloads and reduced internet congestion.
By setting up local update facilities and effectively managing them, you can save valuable organizational internet bandwidth, reduce the load on external update servers, and enhance the efficiency of your network. This approach not only conserves bandwidth but also improves the overall user experience by speeding up update downloads and reducing the risk of update-related disruptions.
Monitoring
Proper monitoring of internet connectivity is crucial for optimizing performance, ensuring network reliability, and quickly identifying and resolving issues. Here are key steps and practices for monitoring internet connectivity for optimized performance:
1. Use Network Monitoring Tools:
- Deploy network monitoring tools that can provide real-time visibility into your network’s performance. These tools can track various metrics, including bandwidth utilization, latency, packet loss, and device health.
2. Establish Baselines:
- Establish performance baselines by monitoring your network during typical usage patterns. This will help you identify deviations from normal behavior and detect potential issues.
3. Monitor Bandwidth Utilization:
- Keep a close eye on bandwidth utilization to ensure that your internet connection is not becoming saturated. Identify bandwidth-hungry applications or users and take corrective actions if necessary.
4. Track Latency and Packet Loss:
- Monitor latency (ping times) and packet loss to assess network responsiveness. High latency or frequent packet loss can impact the user experience and may indicate network congestion or issues.
5. Monitor Network Traffic Patterns:
- Analyze network traffic patterns to identify trends and anomalies. This information can help you make informed decisions about network capacity and optimize resource allocation.
6. Implement Quality of Service (QoS):
- Use QoS settings to prioritize critical applications and services, such as VoIP or video conferencing, over less important traffic. QoS ensures that essential functions have the necessary bandwidth and low latency.
7. Perform Regular Speed Tests:
- Conduct regular speed tests to measure your internet connection’s actual performance compared to its advertised speed. This helps you detect issues with your ISP and validate service level agreements (SLAs).
8. Monitor DNS Resolution:
- Keep an eye on DNS (Domain Name System) resolution times. Slow DNS resolution can lead to delays in accessing websites and services.
9. Set Up Alerts:
- Configure alerts in your network monitoring tools to notify you when specific performance thresholds are breached. Alerts enable you to respond promptly to issues as they arise.
10. Log Analysis:
Review logs generated by routers, switches, and firewalls for clues about network performance issues, security threats, or device errors.
11. Measure End-User Experience:
Consider using end-user experience monitoring tools or surveys to gather feedback on internet performance from employees or customers.
12. Regularly Update Firmware and Software:
Keep network equipment, including routers, switches, and firewalls, up to date with the latest firmware and software updates. This ensures that known issues are addressed.
13. Historical Data Analysis:
Analyze historical performance data to identify long-term trends and plan for network capacity upgrades or optimizations.
14. Disaster Recovery and Redundancy:
Monitor the readiness of disaster recovery and redundancy solutions, such as failover mechanisms, to ensure they are functioning correctly.
15. Security Monitoring:
Continuously monitor network traffic for signs of security threats, including intrusion attempts, malware, and unauthorized access.
16. Documentation:
Maintain detailed documentation of your monitoring procedures, configurations, and the actions taken in response to issues. This documentation is invaluable for troubleshooting and performance optimization.
17. Regular Review and Optimization:
Periodically review your monitoring setup and network performance reports. Use the data to identify areas for improvement and optimize your network infrastructure accordingly.
Effective internet connectivity monitoring not only helps you identify and resolve issues promptly but also allows you to proactively optimize performance, which is crucial for delivering a reliable and efficient network service to your organization.
Routine Maintenance
Routine maintenance of organizational internet connectivity is essential to ensuring that your network is always up and running. By following a few simple steps, you can help to prevent outages and keep your network running smoothly.
Here are some of the things you can do to perform routine maintenance of your organizational internet connectivity:
- Monitor your network traffic. This will help you to identify any potential problems early on.
- Keep your software up to date. This includes your router firmware, firewall software, and any other software that is used to manage your network.
- Scan your network for malware. This will help to protect your network from viruses and other malicious software.
- Back up your data regularly. This will help you to recover your data in case of a disaster.
- Test your backups regularly. This will help to ensure that your backups are working properly.
- Have a plan in place in case of an outage. This will help you to restore your network quickly and minimize the impact of an outage.
By following these steps, you can help to keep your organizational internet connectivity running smoothly and prevent outages.
Here are some additional tips that you can consider:
- Use a network monitoring tool. This can help you to automate the process of monitoring your network traffic and identify potential problems.
- Have a dedicated team responsible for network maintenance. This will help to ensure that the maintenance is done properly and that any problems are addressed quickly.
- Invest in quality hardware and software. This will help to improve the reliability of your network and reduce the risk of outages.
- Train your employees on how to use the network. This will help to prevent accidental damage to the network.
By following these tips, you can help to ensure that your organizational internet connectivity is always up and running.
Service Level Agreements (SLAs)
Service Level Agreements (SLAs) for organizational internet connectivity are formal agreements between an organization and its Internet Service Provider (ISP) that outline the expected level of service, performance, and support for internet connectivity. SLAs are essential for ensuring that your organization receives reliable and consistent internet service. Here are key elements to consider when defining SLAs for internet connectivity:
Service Availability:
- Specify the minimum acceptable uptime percentage, often referred to as the Service Level Objective (SLO). Common SLOs for internet connectivity range from 99.9% to 99.99%. Define how downtime and uptime are measured.
Latency and Packet Loss:
- Define acceptable levels of latency (round-trip delay) and packet loss. These metrics are crucial for real-time applications like VoIP and video conferencing.
Bandwidth and Throughput:
- Specify the minimum guaranteed bandwidth and throughput levels during peak and non-peak hours. Ensure that your organization’s needs are met even during periods of high traffic.
Jitter:
- If your organization relies on real-time communication applications, such as VoIP, define acceptable jitter levels. Jitter refers to variations in the delay of data packets and can affect call quality.
Incident Response and Resolution Times:
- Clearly state the ISP’s responsibilities for responding to and resolving incidents or outages. Define timeframes for acknowledging issues, initiating investigations, and providing estimated resolution times.
Maintenance Windows:
- Specify the ISP’s scheduled maintenance windows and their impact on your organization’s connectivity. Ensure that planned maintenance occurs during non-business hours whenever possible.
Support and Escalation Procedures:
- Describe the ISP’s support channels, including contact methods and hours of availability. Outline the escalation process for unresolved issues and the point of contact for escalation.
Service Credits and Compensation:
- Detail the compensation or service credits that the ISP will provide in the event of SLA violations. This can include prorated billing or additional service credits for extended outages.
Security and Data Protection:
- Include provisions for network security, data protection, and privacy to ensure that the ISP takes adequate measures to safeguard your data and network.
Reporting and Monitoring:
- Define the reporting frequency and content of performance reports provided by the ISP. These reports should include uptime statistics, latency measurements, and incident summaries.
Compliance and Regulations:
- Ensure that the SLA complies with relevant industry regulations and standards, such as data protection regulations or industry-specific requirements.
Termination and Exit Strategy:
- Include terms for contract termination, such as notice periods and procedures for migrating to a new ISP, should you decide to switch providers.
Review and Renewal:
- Specify the frequency of SLA reviews and renewals. SLAs should be reviewed periodically to ensure they align with changing organizational needs.
Dispute Resolution:
- Define a process for resolving disputes or disagreements regarding SLA compliance. This may involve arbitration or mediation.
Documentation and Records:
- Ensure that all SLA terms and agreements are documented in writing and maintained as part of your records.
Service Level Reporting Dashboard:
- Consider implementing a dashboard or portal that allows you to monitor SLA compliance in real time. This can provide transparency and enable proactive management.
Customer Responsibilities:
- Clearly state the responsibilities and requirements of your organization to maintain the agreed-upon SLA. This may include keeping your internal network infrastructure in good working order and promptly reporting issues to the ISP.
Before finalizing an SLA, thoroughly review the terms with your ISP to ensure they accurately reflect your organization’s needs and expectations. Regularly assess SLA compliance and address any discrepancies or issues promptly to maintain a strong and reliable internet connectivity service.
Employee Training and user manual
An Employee Training and User Manual for best practices in Organizational Internet Connectivity is essential for several reasons:
- Maximizing Productivity: In the modern workplace, much of the work relies on internet connectivity. By training employees on best practices, you ensure they can work efficiently and with fewer interruptions, ultimately boosting productivity.
- Reducing Downtime: Internet connectivity issues can lead to significant downtime, costing an organization time and money. Training helps employees understand how to troubleshoot common issues, potentially reducing downtime.
- Security: Proper training can help employees recognize and respond to security threats. Internet security is crucial, and employees need to be aware of practices that protect sensitive data and systems from cyberattacks.
- Consistency: When everyone follows the same best practices, it creates consistency in the workplace. This consistency ensures that network resources are used efficiently and fairly among all employees.
- Resource Management: By training employees on bandwidth management and responsible internet usage, organizations can ensure that network resources are allocated appropriately, preventing bottlenecks caused by excessive use.
- Cost Savings: An efficiently managed network can lead to cost savings. For instance, using best practices for bandwidth management can help reduce data overage charges and unnecessary hardware upgrades.
- Adaptation to New Technologies: Technology is constantly evolving. Training helps employees stay current with new technologies and trends, ensuring that the organization can adapt to new tools and services that require internet connectivity.
- Compliance and Policy Adherence: Training ensures that employees understand and adhere to organizational policies related to internet usage, security, and data protection. This reduces the risk of policy violations and associated consequences.
- Improved User Experience: A well-connected workplace improves the overall user experience for employees. This, in turn, can enhance job satisfaction and employee retention.
- Minimizing Frustration: Internet connectivity problems can be frustrating for employees. Training equips them with the skills to troubleshoot and address issues independently, reducing frustration and the need for IT support.
- Safety and Disaster Recovery: Training can include information on disaster recovery procedures related to internet connectivity. This ensures that employees know what to do in case of network outages or other emergencies.
- Competitive Advantage: In many industries, a stable and high-speed internet connection is a competitive advantage. By following best practices, organizations can offer better service to clients and customers.
- Legal Compliance: Depending on the industry and location, there may be legal requirements related to internet usage and data security. Training helps ensure compliance with these regulations.
- Remote Work Readiness: With the increasing trend of remote work, training in internet connectivity best practices prepares employees to work effectively from various locations.
In summary, an Employee Training and User Manual for best practices in Organizational Internet Connectivity is necessary to ensure that an organization’s internet infrastructure supports its operational needs, safeguards against threats, and maximizes efficiency and productivity. It empowers employees with the knowledge and skills needed to make the most of the organization’s internet resources while minimizing potential issues and risks.
See also
IT System Development, Deployment and Migration – SP Cloud Academy (spca.education)
https://www.cisco.com/c/en_hk/products/security/firewalls/index.html



