A career in cybersecurity is a dynamic and essential field focused on safeguarding digital systems, networks, and data from cyber threats. As technology continues to advance, so do the methods employed by cybercriminals, making cybersecurity professionals indispensable in protecting sensitive information. These experts assess vulnerabilities, develop strategies to mitigate risks, and respond to security incidents. A successful career in cybersecurity requires a deep understanding of hacking techniques, encryption, risk management, and compliance with industry regulations. With a constant demand for skilled professionals, this field offers exciting opportunities, competitive salaries, and the chance to play a critical role in maintaining the integrity of our increasingly digitized world.
Education and Skills to Develop Career in Cyber Security
A successful career in cybersecurity typically requires a combination of education, technical skills, and soft skills. Here’s an overview of the essential components to develop a career in this field:
Education:
- Bachelor’s Degree: Most cybersecurity roles require at least a bachelor’s degree in a related field, such as computer science, information technology, or cybersecurity. Some positions may even prefer or require a master’s degree.
Technical Skills:
a. Network Security:
- Firewall configuration and management
- Intrusion detection and prevention systems (IDS/IPS)
- Virtual Private Networks (VPNs)
- Network architecture and protocols
b. Operating Systems Security:
- Proficiency in Windows, Linux, and other OS security configurations
- Patch management
- Hardening of operating systems
c. Security Software Tools:
- Antivirus and anti-malware tools
- Security Information and Event Management (SIEM) systems
- Vulnerability assessment and scanning tools
d. Cryptography:
- Encryption and decryption techniques
- Public key infrastructure (PKI)
- Cryptographic protocols
e. Secure Coding:
- Awareness of common coding vulnerabilities (e.g., OWASP Top Ten)
- Best practices for writing secure code
- Code review skills
f. Cloud Security:
- Knowledge of cloud platforms (e.g., AWS, Azure, Google Cloud)
- Cloud security services and configurations
- Identity and access management (IAM) in the cloud
g. Mobile Device Security:
- Mobile application security
- Mobile device management (MDM)
- Secure development for mobile platforms
h. Incident Response:
- Incident detection and analysis
- Incident containment and eradication
- Forensic analysis
Information Security Concepts:
a. Risk Management:
- Risk assessment and analysis
- Risk mitigation strategies
- Business impact analysis
b. Compliance and Regulations:
- Knowledge of data protection laws (e.g., GDPR, HIPAA)
- Industry-specific compliance requirements (e.g., PCI DSS)
c. Security Policies and Procedures:
- Development and implementation of security policies
- Security awareness training
Cybersecurity Management Skills:
a. Security Frameworks:
- Familiarity with security frameworks (e.g., NIST Cybersecurity Framework, ISO 27001)
b. Security Governance:
- Security program development and management
- Security risk assessment and management
c. Security Awareness and Training:
- Educating employees about security best practices
- Conducting security drills and exercises
d. Vendor and Third-Party Risk Management:
- Evaluating and managing security risks from third-party vendors
Soft Skills:
a. Communication:
- Effective communication with technical and non-technical stakeholders
- Report writing and documentation
b. Problem-Solving:
- Analytical thinking to identify and address security issues
c. Teamwork:
- Collaboration with cross-functional teams
- Incident response coordination
Continuous Learning and Adaptation:
a. Cyber Threat Intelligence:
- Staying updated on the latest cybersecurity threats and trends
b. Certifications:
- Pursuing relevant certifications (e.g., CISSP, CISM, CompTIA Security+)
c. Professional Development:
- Attending conferences and workshops
- Participating in cybersecurity communities and forums
Remember that cybersecurity is a dynamic field, and staying current with emerging threats and technologies is crucial for success. Additionally, the specific skills required may vary depending on your role within the cybersecurity domain, whether you’re a penetration tester, security analyst, incident responder, or in another role.
Opportunities and Challenges to Build up Career in Cyber Security
Building a career in cybersecurity offers numerous opportunities but also comes with its fair share of challenges. Here’s an overview of both aspects:
Opportunities:
- High Demand: The demand for cybersecurity professionals continues to soar as cyber threats become more sophisticated. Organizations across industries are actively seeking skilled individuals to protect their digital assets.
- Diverse Roles: The field of cybersecurity offers a wide range of roles, from penetration testers and incident responders to security analysts and architects. This diversity allows professionals to find a niche that aligns with their interests and strengths.
- Competitive Salaries: Cybersecurity experts command competitive salaries due to their specialized skills and the critical nature of their work. Compensation tends to be above-average in comparison to many other IT fields.
- Global Opportunities: Cybersecurity is a global concern, and professionals with the right skills can find opportunities worldwide. This global reach can lead to exciting international career prospects.
- Career Advancement: With experience and expertise, cybersecurity professionals can progress to higher-level positions such as security manager, chief information security officer (CISO), or security consultant.
- Constant Learning: The ever-evolving nature of cyber threats means that cybersecurity professionals are continually learning and staying up-to-date with the latest trends and technologies, which can be intellectually rewarding.
Challenges:
- Skill Gap: There is a significant shortage of skilled cybersecurity professionals, which can create intense competition among organizations for qualified candidates. This shortage is a challenge for both employers and job seekers.
- Evolution of Threats: Cyber threats are constantly evolving, requiring cybersecurity experts to adapt and develop new skills to stay ahead of malicious actors.
- Workload and Stress: The high-stress environment of responding to security incidents and the responsibility of safeguarding critical systems can lead to burnout for some professionals.
- Continuous Learning: The need to stay current with rapidly changing technologies and threats can be demanding and time-consuming. Cybersecurity professionals must commit to ongoing education.
- Legal and Ethical Challenges: Ethical considerations are crucial in cybersecurity. Professionals may face dilemmas regarding privacy, hacking, and compliance with regulations.
- Interdisciplinary Skills: Cybersecurity professionals often need to work closely with IT teams, legal departments, and business leaders, requiring strong communication and collaboration skills.
- Adversarial Nature: Cybersecurity professionals are pitted against highly motivated and resourceful adversaries, making it a constant battle to defend against new and innovative attack techniques.
In summary, a career in cybersecurity can be incredibly rewarding due to its high demand, competitive salaries, and opportunities for growth. However, it also involves challenges related to skill gaps, evolving threats, and the need for continuous learning and ethical considerations. Success in this field requires a dedication to staying current, strong problem-solving skills, and a commitment to upholding security and ethical standards.
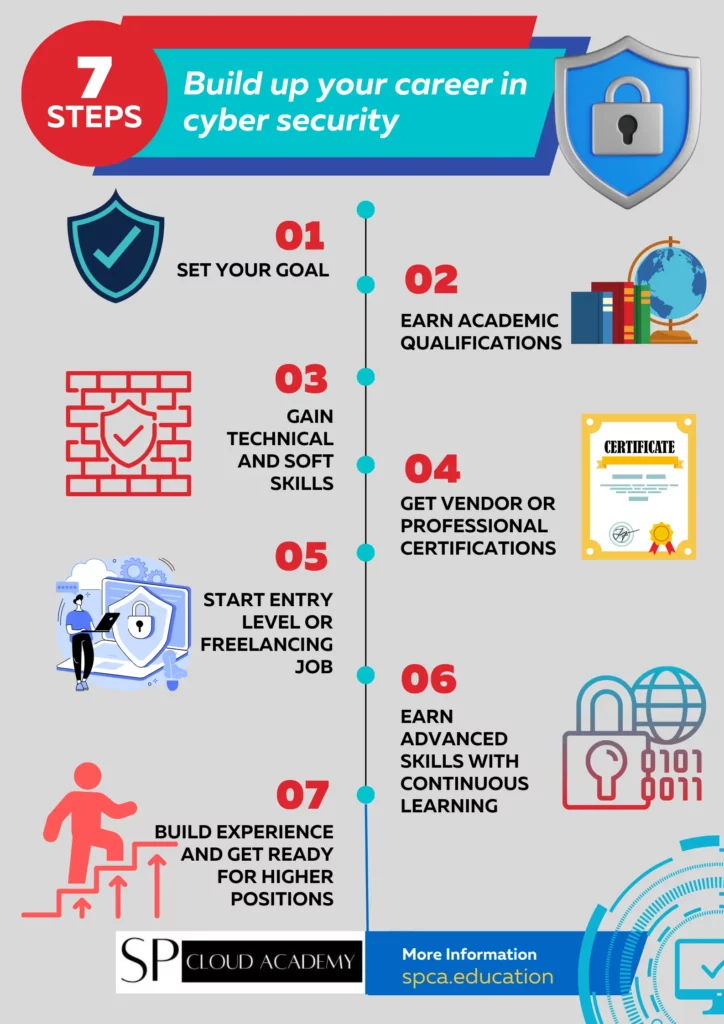
There are many fields in the IT sector. Cyber security is currently a trending field among these. Many people want to pursue a career in the cyber security field but are not aware of the kind of planning and dedication it requires. Cyber Security is a growing and challenging subject where career planning, educational and technical skills, constant self-updating, professional networking, and lifelong learning are essential to build a career.
SP Cloud Academy
Building a career in cybersecurity
Building a career in cybersecurity is a dynamic and rewarding journey that involves safeguarding digital assets and information from an array of ever-evolving threats. As our world becomes increasingly interconnected and reliant on technology, the demand for cybersecurity professionals continues to surge. In this field, you will immerse yourself in the critical task of defending organizations against cyberattacks, data breaches, and vulnerabilities. To succeed, one must acquire a solid foundation in network security, encryption, risk management, and compliance, among other key areas. Continuous learning and adaptability are paramount, as the cybersecurity landscape constantly evolves.
Building a career in cybersecurity involves several key steps:
- Education: Start with a strong educational foundation. Pursue a degree in computer science, information technology, or cybersecurity. Consider advanced degrees for specialized roles.
- Learn the Basics: Gain proficiency in programming, operating systems, and networking fundamentals. Understand cybersecurity concepts and principles.
- Certifications: Acquire industry-recognized certifications like CISSP, CEH, CompTIA Security+, and Cisco CCNA to validate your skills.
- Hands-On Experience: Seek internships, entry-level positions, or volunteer for cybersecurity projects to gain practical experience.
- Specialize: Identify your area of interest (e.g., penetration testing, threat analysis, security architecture) and build expertise in that field.
- Stay Informed: Cyber threats evolve rapidly, so stay updated on the latest trends, vulnerabilities, and security solutions.
- Networking: Connect with professionals in the field, attend conferences, and join cybersecurity organizations to expand your network.
- Soft Skills: Develop communication, problem-solving, and teamwork skills to effectively collaborate and convey security concepts.
- Ethical Behavior: Uphold ethical standards and legal requirements; ethical behavior is fundamental in cybersecurity.
- Build a Portfolio: Showcase your skills through personal projects, GitHub repositories, or a blog.
- Apply for Jobs: Start applying for cybersecurity positions, such as security analyst, junior security engineer, or network administrator.
- Continued Learning: Invest in ongoing education and training to stay competitive.
- Consider Advanced Roles: As you gain experience, explore roles like security architect, incident responder, or security consultant.
- Certify Higher: Pursue advanced certifications like CISSP, CISM, or CISSP-ISSAP as you progress in your career.
- Network Security: Specialize in areas like network security, cloud security, or mobile security, as they become increasingly important.
- Leadership: Aim for leadership roles such as CISO or security manager with experience and additional qualifications.
- Contribute to the Community: Share your knowledge through mentoring, public speaking, or contributing to open-source security projects.
- Cybersecurity Culture: Promote a security-conscious culture within organizations you work for.
- Adaptability: Be adaptable and willing to learn, as the cybersecurity landscape constantly evolves.
- Stay Ethical: Maintain high ethical standards and prioritize protecting data and systems.
Remember that building a career in cybersecurity is a journey that requires dedication, ongoing learning, and a commitment to ethical conduct. It’s a rewarding field that plays a critical role in safeguarding digital environments.
Top Professional and Vendor certifications in Cyber Security
Professional and vendor certifications are crucial for career development in cybersecurity. They validate your expertise, enhancing your credibility and employability. In a competitive field, certifications distinguish you, attracting employers seeking skilled professionals. Certifications like CISSP, CISM, and CompTIA Security+ not only demonstrate your knowledge but also open doors to higher-paying roles. Cybersecurity is ever-evolving, and certifications require continuous learning, keeping you updated on emerging threats and technologies. Compliance and regulatory requirements often mandate certified professionals, making certifications a necessity in some industries. Furthermore, they facilitate professional networking, allowing you to connect with peers and experts. Ultimately, certifications signify your commitment to the field, bolstering your earning potential and global recognition, ensuring a successful career in cybersecurity.
Here are some top cybersecurity certifications, along with their respective vendors, features, descriptions, and official links for more information:





Certified Information Systems Security Professional (CISSP)
- Vendor: (ISC)²
- Description: CISSP is a globally recognized certification for experienced cybersecurity professionals. It covers a wide range of security domains, including risk management, cryptography, and network security.
- Official Link: CISSP Certification
Certified Ethical Hacker (CEH)
- Vendor: EC-Council
- Description: CEH focuses on ethical hacking techniques, tools, and methodologies used by malicious hackers. It equips professionals with the skills to identify and address vulnerabilities.
- Official Link: CEH Certification
Certified Information Security Manager (CISM)
- Vendor: ISACA
- Description: CISM is designed for professionals involved in managing an enterprise’s information security program. It covers risk management, governance, and incident response.
- Official Link: CISM Certification
Certified Information Systems Auditor (CISA)
- Vendor: ISACA
- Description: CISA focuses on auditing, control, and assurance skills for information systems. It’s ideal for professionals involved in auditing and assessing an organization’s IT and business systems.
- Official Link: CISA Certification
CompTIA Security+
- Vendor: CompTIA
- Description: Security+ is an entry-level certification covering foundational security concepts, risk management, cryptography, and network security.
- Official Link: Security+ Certification
These certifications are highly respected and can significantly enhance your cybersecurity career prospects. Visit the provided official links for each certification for detailed information on exam objectives, prerequisites, and study resources.
Cybersecurity Job Roles
Cybersecurity job roles can be categorized into different levels, reflecting the responsibilities, experience, and expertise required. Here are common cybersecurity job levels and their role details:
1. Entry-Level Positions:
a. Security Analyst (Junior Security Analyst):
- Responsibilities: Monitor security alerts, assist in incident detection and response, and conduct routine security tasks. Learn the fundamentals of cybersecurity.
- Skills: Basic knowledge of security concepts, security tools, and strong analytical skills.
- Certifications: CompTIA Security+, Cisco Certified Network Associate (CCNA), Certified Information Systems Security Professional (CISSP) Associate.
b. Security Administrator (Junior Security Administrator):
- Responsibilities: Assist in managing security infrastructure, such as firewalls and anti-virus software. Handle routine security tasks and maintain security policies.
- Skills: Basic network and system administration skills, knowledge of security protocols, and security policy enforcement.
- Certifications: CompTIA Security+, Cisco Certified Network Associate (CCNA), Certified Information Systems Security Professional (CISSP) Associate.
2. Mid-Level Positions:
a. Security Engineer:
- Responsibilities: Design, implement, and manage security systems and protocols. Configure security tools, investigate incidents, and recommend security improvements.
- Skills: Strong networking and security knowledge, security architecture, firewall management, and risk assessment.
- Certifications: Certified Information Systems Security Professional (CISSP), Certified Information Security Manager (CISM), Certified Ethical Hacker (CEH).
b. Security Consultant (Mid-Level Security Consultant):
- Responsibilities: Provide consulting services to clients, conduct security assessments, develop security strategies, and recommend solutions.
- Skills: In-depth knowledge of security frameworks, risk management, and consulting skills.
- Certifications: Certified Information Systems Security Professional (CISSP), Certified Information Security Manager (CISM), Certified Information Systems Auditor (CISA).
c. Incident Responder (Incident Handler):
- Responsibilities: Lead incident response efforts, investigate security incidents, develop and execute response plans, and provide expertise in containment and recovery.
- Skills: Incident handling, digital forensics, malware analysis, and crisis management.
- Certifications: Certified Information Systems Security Professional (CISSP), Certified Incident Handler (ECIH), Certified Computer Examiner (CCE).
3. Senior-Level Positions:
a. Security Architect (Senior Security Architect):
- Responsibilities: Design and oversee an organization’s security architecture, develop security policies, and ensure alignment with business objectives.
- Skills: Advanced security architecture, risk management, and strong knowledge of security technologies.
- Certifications: Certified Information Systems Security Professional (CISSP), Certified Information Security Manager (CISM), Certified Information Systems Auditor (CISA).
b. Chief Information Security Officer (CISO):
- Responsibilities: Lead an organization’s cybersecurity strategy, manage security teams and budgets, and report to executive leadership.
- Skills: Leadership, strategic thinking, risk management, and business acumen.
- Certifications: Certified Information Systems Security Professional (CISSP), Certified Information Security Manager (CISM), Certified Information Systems Auditor (CISA).
4. Expert-Level Positions:
a. Cybersecurity Researcher (Security Researcher):
- Responsibilities: Conduct advanced research to discover new security threats, vulnerabilities, and mitigation techniques. Publish findings and contribute to the field’s knowledge.
- Skills: Research skills, data analysis, and an in-depth understanding of cybersecurity concepts.
- Certifications: Certifications are less common in this role, but relevant certifications may include Certified Information Systems Security Professional (CISSP) or Certified Ethical Hacker (CEH).
Please note that the specific titles and responsibilities may vary between organizations, and the cybersecurity field is continually evolving. Professionals often advance through these levels based on their experience, expertise, and contributions to the field.
Career Development Sample Course
A comprehensive syllabus for a Cybersecurity Career Development course should focus on not only technical skills but also soft skills and strategies for professional growth in the field. Here’s a sample syllabus:
Course Title: Cybersecurity Career Development
Course Description: This course is designed to provide students with the skills, knowledge, and strategies needed for a successful career in cybersecurity. It covers technical skills, industry certifications, career planning, and soft skills development.
Introduction to Cybersecurity Careers
- Overview of cybersecurity roles and specializations
- Job market trends and demand for cybersecurity professionals
- Setting career goals in cybersecurity
Cybersecurity Fundamentals
- Review of essential cybersecurity concepts and principles
- Understanding cyber threats and attack vectors
- Introduction to risk management in cybersecurity
Building a Strong Foundation
- Selecting the right educational path and degrees
- Importance of certifications in cybersecurity careers
- Preparing for and choosing the right certifications
Technical Skills for Cybersecurity
- Network security fundamentals
- Operating system security (Windows, Linux)
- Basics of programming and scripting
Cybersecurity Tools and Technologies
- Overview of common security tools (firewalls, IDS/IPS, SIEM)
- Security software and hardware solutions
- Hands-on experience with security tools
Ethical Hacking and Penetration Testing
- Understanding ethical hacking and penetration testing
- Introduction to popular penetration testing tools
- Preparing for the Certified Ethical Hacker (CEH) certification
Incident Response and Handling
- Incident response processes and methodologies
- Developing an incident response plan
- Handling real-world security incidents
Secure Coding and Web Application Security
- Importance of secure coding practices
- Common web application vulnerabilities
- Strategies for securing web applications
Cloud Security and Emerging Technologies
- Security challenges in cloud computing
- Security considerations for emerging technologies (IoT, AI)
- Staying updated with the latest cybersecurity trends
Soft Skills for Cybersecurity Professionals
- Communication and presentation skills
- Problem-solving and critical thinking
- Ethical considerations and professional conduct
Resume Building and Job Search
- Crafting an effective cybersecurity resume
- Strategies for job searching in the cybersecurity field
- Interview preparation and techniques
Networking and Professional Development
- Building a professional network in cybersecurity
- Leveraging social media and online communities
- Mentoring and career advancement strategies
Industry Certifications and Continuing Education
- In-depth review of industry-recognized certifications
- Selecting certifications aligned with career goals
- Creating a personalized certification roadmap
Career Planning and Goal Setting
- Creating a long-term career plan in cybersecurity
- Goal setting and strategies for achieving career milestones
- Balancing work, life, and professional development
Capstone Project
- Students work on a cybersecurity career development project, which may include creating a career portfolio, a personal website, or a career plan.
Assessment: Assessment in this course may include quizzes, assignments, a final project, class participation, and presentations.
Please note that the course syllabus can be adapted and customized based on the specific needs of the students and the course objectives. Career development is a vital aspect of a successful cybersecurity career, and this course should equip students with both technical and soft skills required to thrive in the field.
Cyber security learning sourses
Here are some of the top cybersecurity learning sources in detail, along with their links:
Cybrary:
- Details: Cybrary offers a wide range of free and paid cybersecurity courses. They cover various aspects of cybersecurity, from basic concepts to advanced topics like penetration testing and ethical hacking.
- Link: Cybrary
Coursera – Cybersecurity Specializations:
- Details: Coursera collaborates with top universities and organizations to offer comprehensive cybersecurity specializations. These courses cover various areas of cybersecurity, including network security, cryptography, and risk management.
- Link: Coursera Cybersecurity Specializations
edX – Cybersecurity Courses:
- Details: edX provides a wide array of cybersecurity courses from top institutions like MIT, Harvard, and more. These courses cover topics such as ethical hacking, secure coding, and cybersecurity risk management.
- Link: edX Cybersecurity Courses
SANS Institute:
- Details: SANS is renowned for its cybersecurity training and certifications. They offer both online and in-person courses, with a strong emphasis on hands-on training and real-world scenarios.
- Link: SANS Institute
Pluralsight – Cybersecurity Training:
- Details: Pluralsight provides a vast library of IT and cybersecurity courses, suitable for beginners to experts. Their courses cover various cybersecurity domains, including cloud security and threat hunting.
- Link: Pluralsight Cybersecurity Training
MIT OpenCourseWare:
- Details: MIT offers free course materials for various cybersecurity-related courses, including lecture notes, assignments, and readings. It’s an excellent resource for those seeking in-depth technical knowledge.
- Link: MIT OpenCourseWare – Cybersecurity
Cybersecurity and Infrastructure Security Agency (CISA):
- Details: CISA offers a variety of free resources and training materials, including webinars, toolkits, and best practice guides. These resources are particularly useful for U.S. government employees and contractors.
- Link: CISA Cybersecurity Training and Resources
Certified Information Systems Security Professional (CISSP) Official Study App:
- Details: ISC², the organization behind CISSP, offers an official study app that includes practice questions and flashcards to help you prepare for the CISSP exam.
- Link: CISSP Official Study App
Cisco Networking Academy:
- Details: Cisco Networking Academy provides free online courses in networking and cybersecurity. It’s an excellent resource for those looking to build a strong foundation in network security.
- Link: Cisco Networking Academy
Cybersecurity Learning Forums and Communities:
- Details: Engaging with cybersecurity communities like Reddit’s r/cybersecurity and the Stack Exchange Information Security community can provide valuable insights, discussions, and resources.
Please note that the availability and details of these courses may change over time, so it’s essential to visit the provided links for the most up-to-date information on course content, fees, and enrollment procedures. Additionally, some courses may offer free audit options or financial assistance for those who qualify.
Cyber security labs
Cybersecurity labs are specialized environments where individuals can gain hands-on experience and practical skills in various aspects of cybersecurity. These labs simulate real-world scenarios, allowing users to practice and improve their cybersecurity knowledge and skills in a controlled and safe environment. Here are some common types of cybersecurity labs and platforms:
Capture The Flag (CTF) Labs:
- Hack The Box (HTB): HTB provides a platform where users can access a range of vulnerable virtual machines and challenges to solve. It’s suitable for both beginners and advanced users.
- TryHackMe: TryHackMe offers a variety of virtual rooms and CTF challenges designed to teach and test cybersecurity skills. They often include guided learning paths.
- OverTheWire: OverTheWire hosts several war games, such as Bandit and Narnia, which focus on various aspects of cybersecurity and hacking.
Penetration Testing Labs:
- Metasploit Unleashed: Metasploit Unleashed is a free training resource that provides a virtual lab environment for learning and practicing penetration testing techniques using the Metasploit framework.
- PentesterLab: PentesterLab offers web penetration testing labs and exercises for beginners and professionals.
Cloud-Based Labs:
- AWS, Azure, and Google Cloud Labs: Major cloud providers offer hands-on labs and playgrounds where users can practice securing cloud environments, including configuring security groups, IAM policies, and more.
- Qwiklabs: Qwiklabs offers hands-on labs for Google Cloud Platform (GCP) and is useful for those interested in cloud security.
Networking Labs:
- GNS3: GNS3 is a network simulation tool that allows users to create complex network topologies for practicing network security and configuration.
- Cisco Packet Tracer: Cisco Packet Tracer is a network simulator primarily used for learning Cisco networking and security technologies.
Vulnerable VMs and Labs:
- OWASP WebGoat and OWASP Juice Shop: These deliberately vulnerable web applications are used to practice web application security testing and exploitation.
- DVWA (Damn Vulnerable Web Application): DVWA is a PHP/MySQL web application intentionally designed with security vulnerabilities for testing and training.
Enterprise-Grade Labs:
- Some organizations and educational institutions set up their own enterprise-grade labs to simulate complex security scenarios, such as advanced persistent threats (APTs) and incident response exercises.
Online Cybersecurity Training Platforms:
- Platforms like Cybrary, Pluralsight, and LinkedIn Learning offer hands-on labs as part of their cybersecurity courses and training programs.
When using these cybersecurity labs, it’s essential to have a strong understanding of ethical considerations and legal implications. Always use these resources responsibly and only on systems and networks you have explicit permission to access. Additionally, many of these labs may require accounts or subscriptions, so be sure to review their specific terms and conditions.
Conclusion
In today’s IT job market, the demands of the cybersecurity profession are more pronounced than ever. With the increasing frequency and sophistication of cyberattacks, organizations are seeking cybersecurity experts who can provide robust protection for their digital assets. These professionals must possess up-to-date technical expertise, continuously adapting to new threats and technologies. Analytical skills are paramount, as they must swiftly detect and respond to security incidents. Effective communication is vital for conveying complex security concepts to diverse stakeholders. Ethical considerations and compliance knowledge are crucial, especially with stringent data protection regulations like GDPR. The ability to work collaboratively across teams and the 24/7 availability for incident response add to the profession’s demands. Certifications remain valuable for validating skills in this rapidly evolving field, making cybersecurity a challenging yet rewarding career choice in the current IT job market.
FAQs
Here are some frequently asked questions (FAQs) about a career in cybersecurity:
What is cybersecurity?
- Cybersecurity is the practice of protecting computer systems, networks, and data from theft, damage, or unauthorized access. It encompasses various technologies, processes, and practices to ensure the security of digital environments.
Why is cybersecurity important?
- Cybersecurity is crucial to safeguard sensitive information, prevent data breaches, and protect critical infrastructure. It helps maintain the confidentiality, integrity, and availability of digital assets.
What are the different career paths in cybersecurity?
- There are various career paths in cybersecurity, including security analyst, ethical hacker, penetration tester, security engineer, security architect, incident responder, and security consultant.
What qualifications do I need for a career in cybersecurity?
- A bachelor’s degree in computer science, information technology, or cybersecurity is typically required. Certifications like CISSP, CEH, CompTIA Security+, and relevant experience can also enhance your qualifications.
Do I need programming skills for a career in cybersecurity?
- Proficiency in programming languages like Python, C++, and Java is beneficial, especially for roles like penetration testers and security researchers. However, not all cybersecurity roles require extensive programming skills.
Are certifications necessary for a cybersecurity career?
- Certifications are highly recommended in cybersecurity. They validate your skills and knowledge, making you more competitive in the job market. Common certifications include CISSP, CEH, CompTIA Security+, and more.
How do I gain practical experience in cybersecurity?
- You can gain experience through internships, entry-level positions, participating in Capture The Flag (CTF) competitions, volunteering for cybersecurity projects, or setting up your own lab to practice.
What are the biggest challenges in cybersecurity careers?
- Cyber threats are constantly evolving, requiring professionals to stay updated. The shortage of skilled cybersecurity professionals is also a challenge. The field can be high-stress, and ethical dilemmas may arise.
How can I stay current in the field of cybersecurity?
- Stay informed through blogs, podcasts, industry news, and attending cybersecurity conferences. Continuous learning and pursuing advanced certifications are also essential.
What is the earning potential in cybersecurity?
- Salaries in cybersecurity can vary widely based on factors like location, experience, and specialization. Generally, cybersecurity professionals earn competitive salaries due to the high demand for their skills.
Is there room for career advancement in cybersecurity?
- Yes, cybersecurity offers room for career growth. With experience and expertise, you can advance to higher-level positions such as security manager, CISO, or security consultant.
Is a background check required for a career in cybersecurity?
- Many employers in the cybersecurity field conduct background checks on prospective employees to ensure trustworthiness and security clearances for certain roles.
Is cybersecurity a 9-to-5 job?
- While some cybersecurity roles follow a standard work schedule, many require 24/7 monitoring and incident response, making them more dynamic and potentially involving irregular hours.
Can I transition into cybersecurity from another IT field?
- Yes, transitioning from another IT field is possible. Relevant experience and certifications can help you make the switch.
How can I contribute to the cybersecurity community?
- You can contribute by sharing knowledge through mentoring, presenting at conferences, contributing to open-source projects, and advocating for cybersecurity awareness.
A career in cybersecurity offers a wide range of opportunities and challenges, making it an exciting and rewarding field for those passionate about protecting digital assets and information.
References
Learn to become a modern Cyber Security Expert by following the steps, skills, resources and guides listed in this roadmap.
https://roadmap.sh/cyber-security
IBM Cybersecurity Analyst Professional Certificate
https://www.coursera.org/professional-certificates/ibm-cybersecurity-analyst
See Also
Security Archives – SP Cloud Academy (spca.education)
-

Top 10 Best Patch Management Software for 2025: Features, Pricing, and Expert Picks!
-

The Ultimate Guide to Securing Your System with BitLocker, Windows Defender, and Firewall Rules
-

Stay Secure Anytime, Anywhere: Remote Monitoring with IP-Based CCTV and Cloud Integration
-

Unlocking the Dark Web: A Deep Dive into All Types of Cyber Threats
-

How McAfee Total Protection Shields You from Cyber Threats
-
How to Set Up and Use Google Password Manager for Enhanced Security
